In the Linux operating system, file and directory permissions are key to securing files and controlling access. The chmod command (short for “change mode”) is used to modify these permissions, and it’s one of the most frequently used tools for system administrators and power users. Knowing how to use chmod effectively is crucial for managing who can read, write, or execute files and directories on your system.
1.What are Directory Permissions in Linux?
There are three types of permissions that can be applied to a directory:
1. Read (r) – r (4)
- For Files: Allows the user to view the contents of the file.
- For Directories: Grants permission to list the files and subdirectories inside the directory (
lscommand).
2. Write (w) – w (2)
- For Files: Allows the user to modify the contents of the file.
- For Directories: Grants permission to create, delete, or rename files and subdirectories within the directory.
3. Execute (x) – x (1)
- For Files: Allows the user to execute the file if it is a script or binary.
- For Directories: Allows the user to navigate into the directory (using
cdto change the directory).
User Categories
Linux permissions apply to three categories of users:
- Owner: The user who owns the file or directory.
- Group: A set of users who share the same permissions for the file or directory.
- Others: All other users who are not the owner or in the group.
Understanding Permissions with ls -l
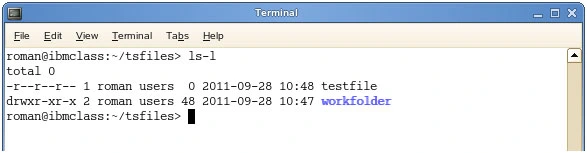
When you use the ls -l command, it displays the permissions in a format like this:
sqlCopy codedrwxr-xr-x 2 user group 4096 Nov 21 12:30 directory_name
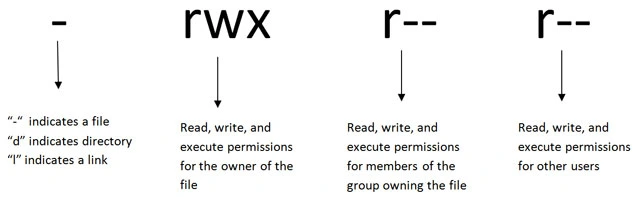
- The first character (
d) indicates it’s a directory. - The next 9 characters (
rwxr-xr-x) represent the permissions:- The first 3 characters (
rwx) represent permissions for the owner (read, write, execute). - The next 3 characters (
r-x) represent permissions for the group (read, execute). - The last 3 characters (
r-x) represent permissions for others (read, execute).
- The first 3 characters (
Numerical Representation of Permissions
Permissions can also be represented numerically:
- Read = 4
- Write = 2
- Execute = 1
Each category of users (owner, group, others) has a value, and the sum of the values determines the permissions. For example:
7=rwx(4 + 2 + 1)5=r-x(4 + 0 + 1)6=rw-(4 + 2 + 0)
So, a permission of 755 means:
- Owner:
rwx(7) - Group:
r-x(5) - Others:
r-x(5)
Modifying Permissions
To modify directory permissions, the chmod command is used. Example:
chmod 755 directory_name— sets the permissions torwxr-xr-xfor the directory.chmod u+x directory_name— adds execute permission to the owner.
2. How to Use the chmod Command
1. Symbolic Mode
In symbolic mode, you specify the user categories (owner, group, others) and the permissions (read, write, execute) using symbols.
Syntax:
cssCopy codechmod [who][operator][permissions] file_name
- who: Specifies the users who will have the permission changed:
u: User (owner)g: Groupo: Othersa: All users (user, group, others)
- operator: Specifies how to modify the permissions:
+: Adds the permission-: Removes the permission=: Sets the permission exactly (replaces existing permissions)
- permissions: Specifies the permission to be added or removed:
r: Readw: Writex: Execute
Examples:
- Add execute permission to the owner:bashCopy code
chmod u+x file_nameThis adds execute permission to the owner. - Remove write permission from others:bashCopy code
chmod o-w file_nameThis removes write permission from others. - Give read and execute permission to everyone:bashCopy code
chmod a+rx file_nameThis adds read and execute permissions for the owner, group, and others. - Set read and write permissions for the owner, and read-only for the group:bashCopy code
chmod u=rw,g=r file_nameThis sets the owner’s permissions to read and write, while the group gets only read permission.
2. Numeric (Octal) Mode
In numeric mode, permissions are represented by a three-digit octal number, where each digit represents the permissions for the owner, group, and others, respectively.
Each permission is represented by a number:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
To determine the numeric value for each user category, you add the numbers corresponding to the permissions:
rwx= 4 + 2 + 1 = 7rw-= 4 + 2 + 0 = 6r--= 4 + 0 + 0 = 4---= 0 + 0 + 0 = 0
Syntax:
bashCopy codechmod [permissions] file_name
The permission is expressed as a three-digit octal number, where each digit corresponds to the permissions for the owner, group, and others.
Examples:
- Set full permissions for the owner, and read and execute permissions for group and others:bashCopy code
chmod 755 file_nameThis sets:- Owner:
rwx(7) - Group:
r-x(5) - Others:
r-x(5)
- Owner:
- Set read and write permissions for the owner, and read-only for group and others:bashCopy code
chmod 644 file_nameThis sets:- Owner:
rw-(6) - Group:
r--(4) - Others:
r--(4)
- Owner:
- Set no permissions for others:bashCopy code
chmod 700 file_nameThis sets:- Owner:
rwx(7) - Group:
---(0) - Others:
---(0)
- Owner:
3. Changing Directory Permissions
You can also use chmod to modify directory permissions. When you apply permissions to a directory, the execute permission (x) allows a user to enter or change into the directory (using cd).
For example:
- Give the owner full permissions, but only read and execute for group and others:bashCopy code
chmod 755 directory_name
4. Recursively Changing Permissions
You can use the -R option with chmod to apply the changes recursively to all files and subdirectories within a directory.
Syntax:
bashCopy codechmod -R [permissions] directory_name
Example:
- Set read and write permissions for the owner and group, and read-only for others on all files in a directory:bashCopy code
chmod -R 664 directory_name
This applies rw-rw-r-- permissions to all files and subdirectories inside directory_name.

3. Applying Permissions Recursively
In some cases, you may need to change permissions not just for a directory, but also for all the files and subdirectories inside it. This can be done with the -R (recursive) option, which applies the chmod command to the directory and all its contents.
Syntax:
bashCopy codechmod -R [permissions] directory_name
Explanation:
-R: This option stands for “recursive,” meaning the command will apply the permissions to the directory and all files and subdirectories within it.[permissions]: This specifies the permissions you want to apply (in symbolic or numeric format).directory_name: This is the name of the directory for which you want to change permissions.
Examples:
- Set read and write permissions for the owner, and read-only for group and others, recursively:bashCopy code
chmod -R 644 directory_nameThis will set the permissions of all files and subdirectories insidedirectory_nametorw-r--r--. - Grant execute permission to the owner of all files and directories recursively:bashCopy code
chmod -R u+x directory_nameThis adds the execute permission to the owner of all files and subdirectories inside the directory. - Set full permissions for the owner, and only read and execute permissions for group and others, recursively:bashCopy code
chmod -R 755 directory_nameThis will set the permissions of all files and subdirectories insidedirectory_nametorwxr-xr-x. - Remove write permission for others in all files and subdirectories within a directory:bashCopy code
chmod -R o-w directory_nameThis will remove the write permission from others for all files and subdirectories insidedirectory_name.
Important Notes:
- Be cautious when using
chmod -R, especially with directories containing sensitive files. Changing permissions recursively can unintentionally expose sensitive files to unintended users or disrupt the functionality of certain files that require specific permissions. - If you only want to apply permissions to directories and not to files, you can combine
chmod -Rwithfind:bashCopy codefind directory_name -type d -exec chmod 755 {} \;This will apply755(read, write, and execute for the owner, and read and execute for group and others) only to directories.
How to Change Directory Permissions in Linux with chmod: A Comprehensive Guide
In the Linux operating system, file and directory permissions are key to securing files and controlling access. The chmod command (short for “change mode”) is used to modify these permissions, and it’s one of the most frequently used tools for system administrators and power users. Knowing how to use chmod effectively is crucial for managing who can read, write, or execute files and directories on your system.
This blog post will walk you through the basics of changing directory permissions with chmod, explaining both symbolic and numeric methods, how to apply permissions recursively, and best practices for securing your system.
1. What are Directory Permissions in Linux?
In Linux, directories have three basic permissions:
- Read (
r): Allows the user to list the contents of a directory. - Write (
w): Allows the user to add or remove files within the directory. - Execute (
x): Allows the user to enter the directory and access the files inside (also required to open a directory with commands likecd).
Permissions are set for three categories of users:
- Owner: The user who owns the directory.
- Group: A set of users who share the same group.
- Others: All users who do not fall into the owner or group categories.
A directory’s permissions are displayed in the following format:
Copy codedrwxr-xr-x
- The first character (
d) indicates that it is a directory. - The next three characters (
rwx) represent the owner’s permissions. - The next three (
r-x) represent the group’s permissions. - The last three (
r-x) represent others’ permissions.
In this example, the owner has read, write, and execute permissions, while the group and others have read and execute permissions.
2. How to Use the chmod Command
The chmod command allows you to modify file and directory permissions in Linux. It can be used with either symbolic or numeric modes.
2.1 Symbolic Mode
In symbolic mode, you use characters to represent permissions:
r= readw= writex= execute
The symbolic mode has three components:
- Who: Specifies who the permission applies to:
u= user (owner)g= groupo= othersa= all (owner, group, and others)
- Operator: Specifies how to change the permissions:
+= add permission-= remove permission== set exact permission (overwrite existing permissions)
- Permissions: Specifies which permissions to modify:
r= readw= writex= execute
Examples of Symbolic Mode Usage:
1. Granting Read, Write, and Execute Permissions to the Owner
To grant the owner full access (read, write, and execute), use:
bashCopy codechmod u+rwx directory_name
2. Granting Execute Permission to the Group
To give execute permissions to the group:
bashCopy codechmod g+x directory_name
3. Revoking Write Permission for Others
To remove write access from others:
bashCopy codechmod o-w directory_name
4. Setting Permissions for All Users
To grant read and execute permissions to everyone, but remove all write permissions:
bashCopy codechmod a=rx directory_name
2.2 Numeric (Octal) Mode
In numeric mode, permissions are represented by numbers. Each permission is assigned a value:
- Read (
r) = 4 - Write (
w) = 2 - Execute (
x) = 1 - No permission (
-) = 0
To set permissions, add up the values for the desired permissions for each user category:
- Owner (User): First digit
- Group: Second digit
- Others: Third digit
For example:
- 7 =
rwx(4 + 2 + 1) - 6 =
rw-(4 + 2) - 5 =
r-x(4 + 1) - 4 =
r--(4)
Examples of Numeric Mode Usage:
1. Full Permissions for Owner, Read-Only for Group and Others
To grant full access to the owner, and read-only access to the group and others:
bashCopy codechmod 744 directory_name
2. Granting Read and Execute Permissions for All Users
To allow the owner, group, and others to read and execute the directory, but not write to it:
bashCopy codechmod 755 directory_name
3. Removing Permissions for Others
To remove all permissions for others and leave the owner and group with full access:
bashCopy codechmod 770 directory_name
3. Applying Permissions Recursively
In some cases, you may need to change permissions not just for a directory, but also for all the files and subdirectories inside it. This can be done with the -R (recursive) option, which applies the chmod command to the directory and all its contents.
Example: Granting Execute Permission Recursively
If you want to add execute permissions for all users (owner, group, and others) to a directory and all its subdirectories and files, run:
bashCopy codechmod -R a+x directory_name
Be cautious when using the recursive option, especially with sensitive directories or system files, as it can accidentally expose data or grant unwanted access.
4. Verifying Permissions
Using the ls -l Command
The ls -l command is the most common way to verify the permissions of a file or directory. This command lists files in a directory in long format, including detailed information about permissions.
Syntax:
bashCopy codels -l [file_name or directory_name]
Example:
bashCopy codels -l myfile.txt
Output:
csharpCopy code-rwxr-xr-- 1 user group 2048 Nov 21 12:00 myfile.txt
- The first column represents the permissions:
-indicates a regular file (it could be adfor a directory,lfor a symbolic link, etc.).- The next 9 characters represent permissions for owner, group, and others:
rwx: Read, write, and execute permissions for the owner.r-x: Read and execute permissions for the group.r--: Read-only permissions for others.
- The remaining columns show the owner, group, file size, modification date, and file name.
Using stat Command
The stat command provides detailed information about a file, including its permissions, ownership, and more.
Syntax:
bashCopy codestat [file_name or directory_name]
Example:
bashCopy codestat myfile.txt
Output:
yamlCopy code File: myfile.txt
Size: 2048 Blocks: 8 IO Block: 4096 regular file
Device: 801h/2049d Inode: 1234567 Links: 1
Access: 2024-11-21 12:00:00.000000000
Modify: 2024-11-21 12:00:00.000000000
Change: 2024-11-21 12:00:00.000000000
Birth: -
Permissions: -rwxr-xr--
User: user
Group: group
- Permissions:
-rwxr-xr--indicates the file’s permissions. - User: The owner of the file (
user). - Group: The group associated with the file (
group).
Checking Directory Permissions
For directories, you can also use ls -ld to view the permissions for the directory itself, not the contents inside it.
Example:
bashCopy codels -ld /path/to/directory
Output:
sqlCopy codedrwxr-xr-x 2 user group 4096 Nov 21 12:00 directory_name
- The first character (
d) indicates it’s a directory. - The rest of the output shows the permissions for the directory, including the owner, group, and other information.
Using getfacl for Access Control Lists (ACLs)
If the system uses ACLs (Access Control Lists), you can use getfacl to view more granular permission settings, especially when standard chmod permissions are not enough.
Syntax:
cssCopy codegetfacl [file_name or directory_name]
Example:
Copy codegetfacl myfile.txt
Output:
arduinoCopy code# file: myfile.txt
# owner: user
# group: group
user::rwx
group::r-x
other::r--
- The output shows ACLs for the file. This can be useful in complex permission setups, especially when using multiple users and groups with specific access controls.
Verifying Permissions Recursively
To verify the permissions for all files and subdirectories inside a directory recursively, use the ls -lR command.
Syntax:
bashCopy codels -lR [directory_name]
Example:
bashCopy codels -lR /path/to/directory
This will display the permissions for all files and subdirectories inside directory_name and its subdirectories, making it easy to verify permissions across an entire directory structure.
5. Best Practices for Using chmod
Principle of Least Privilege
Always apply the principle of least privilege when assigning permissions. This means that users and groups should only have the minimum permissions necessary to perform their tasks. For example:
- Do not grant write permission to others unless absolutely necessary.
- Restrict execute permissions to trusted users and groups, especially for sensitive files and directories.
Use Numeric Permissions Sparingly
While numeric permissions (e.g., 755, 644) are convenient, they can sometimes be harder to understand at a glance. Use symbolic permissions when the intention is to be clearer or when fine-grained control is needed. For example:
chmod u+x file_nameis more readable thanchmod 755 file_namewhen granting execute permission to the owner.- Use numeric permissions for quick setups when you’re comfortable with the numbers.
Be Careful with chmod -R (Recursive Option)
The chmod -R command can be a time-saver when applying permissions to a whole directory structure, but it also carries the risk of unintentionally altering permissions inappropriately. Always be cautious:
- Double-check the directory or files you’re applying the command to.
- Test on a smaller set of files first to ensure it works as intended.
- Avoid giving full access (777) to directories or files that don’t require it, as this opens up security risks.
Review Permissions Regularly
Regularly audit file and directory permissions, especially for important or sensitive files, to ensure that permissions haven’t been unintentionally modified. For example, run ls -lR on sensitive directories and review access control lists (ACLs) with getfacl when applicable.
Avoid Giving 777 Permissions
Granting 777 permissions (read, write, and execute for everyone) is risky because it allows any user to modify or execute the file, potentially exposing your system to security vulnerabilities. Instead:
- Use more restrictive permissions like
755for executable files and directories. - Use
644for regular files when write permissions aren’t needed by everyone.
Apply Permissions to Directories as Needed
For directories, make sure to carefully consider whether execute permission (x) is granted:
- For directories, execute permission allows users to enter the directory (
cd), so always include execute permission on directories when it is needed to allow users to access files within the directory. - For files, execute permission (
x) is only needed for files that are meant to be run as programs or scripts.
Use ACLs for Complex Permission Scenarios
When you need more detailed control over file permissions than the standard chmod model allows, use Access Control Lists (ACLs). ACLs allow you to set permissions for specific users or groups on individual files or directories, providing greater granularity.
To view ACLs, use:
Copy codegetfacl file_name
To set ACLs, use:
Copy codesetfacl -m u:username:rwx file_name
Document Permission Changes
Whenever you change permissions, especially in critical directories, consider documenting the changes. This is useful for:
- Tracking permission changes over time.
- Collaboration: Other administrators or users need to know why certain permissions were applied.
- Restoration: If permissions are accidentally changed, having a record of what they were originally can be helpful.
Limit Permissions for Configuration Files
Configuration files (e.g., those in /etc/) often contain sensitive system settings. Ensure that:
- Only the root user or a specific admin group has write access.
- Read access may be required for certain users or services, but write access should be limited to avoid accidental or unauthorized changes.
Apply the umask Setting
The umask command defines the default permissions applied when creating new files. For example, you can set the umask to restrict new files from being writable by others.
- A common default
umaskvalue is022, which means new files will haverw-r--r--permissions (644), and new directories will haverwxr-xr-x(755). - To set the
umask, use:bashCopy codeumask 022
Use Groups for Managing Permissions
Rather than assigning permissions to individual users, consider using groups to manage access more efficiently. Group-based permissions are easier to manage and scale, especially on larger systems. For example:
- Add users who need similar access to a specific group.
- Assign permissions to the group (e.g.,
chmod g+rw file_name).
Use chown and chgrp for Ownership
In conjunction with chmod, the chown (change owner) and chgrp (change group) commands allow you to assign proper ownership of files and directories. Always ensure that files and directories have the correct owner and group, especially in shared environments.
Example:
sqlCopy codechown user:group file_name
6.Common Mistakes to Avoid
Granting 777 Permissions
- Mistake: Setting file or directory permissions to
777(read, write, and execute for everyone).- Problem: This gives all users full access to the file, allowing anyone to modify, delete, or execute it. It can result in security vulnerabilities, as malicious users or processes can alter the file’s contents or execute it.
- Solution: Always prefer more restrictive permissions, such as
755for directories (where users can enter and execute but cannot modify) or644for files (readable by everyone, writable only by the owner).
chmod 755 directory_name chmod 644 file_name
Changing Permissions Recursively Without Caution (chmod -R)
- Mistake: Using
chmod -Rto apply changes recursively without understanding the impact.- Problem:
chmod -Rchanges permissions for all files and subdirectories in a directory. This can unintentionally grant permissions to sensitive files or folders, potentially causing security risks. - Solution: Double-check the directory and file structure before using
chmod -R. Always ensure you’re applying permissions to the correct directory, and consider testing on a smaller set of files first.
chmod -R 755 /path/to/directory - Problem:
Giving Write Permissions to Others (o+w)
- Mistake: Granting write permission to others (e.g.,
chmod o+w file_name).- Problem: Giving write permission to others can allow unauthorized users to modify or delete files, leading to potential data corruption or unauthorized changes.
- Solution: Avoid giving write access to “others” unless absolutely necessary. Typically, files should only be writable by the owner and possibly by the group.
chmod o-w file_name # Remove write permission for others
Not Applying Execute Permissions for Directories
- Mistake: Forgetting to apply execute (
x) permissions to directories when necessary.- Problem: Without the execute permission, users won’t be able to access the contents of a directory, even if they have read permissions.
- Solution: When setting permissions for directories, make sure that execute permission is granted to the relevant users or groups, especially if they need to navigate into the directory.
chmod 755 directory_name # Ensure execute permission for directories
Using Numeric Permissions Without Understanding
- Mistake: Using numeric permissions without understanding how they map to the actual permissions.
- Problem: Numeric permissions can be difficult to read and understand at a glance. For example,
chmod 777may seem fine if you are trying to give full access to a directory, but it may unintentionally give full write permissions to others as well, compromising security. - Solution: If you’re unsure about numeric permissions, prefer using symbolic notation, as it’s more intuitive. Use
chmodwith the+,-, or=operators to set specific permissions.
chmod u+x file_name # Use symbolic notation for clarity - Problem: Numeric permissions can be difficult to read and understand at a glance. For example,
Changing Ownership Without Verifying
- Mistake: Using
chownorchgrpto change ownership of files or directories without verifying the proper owner or group.- Problem: Changing ownership of files or directories incorrectly can lead to access control issues, preventing the correct user or service from accessing the resources. This can break system processes or cause other problems.
- Solution: Always verify the ownership needs before changing ownership. Use
chowncarefully to ensure that files are owned by the correct user or group.
chown user:group file_name # Ensure the correct owner and group are set
Granting Permissions to Sensitive System Files
- Mistake: Applying permissions to sensitive system files (e.g.,
/etc/passwd,/etc/shadow) that could grant unauthorized users access.- Problem: Allowing non-privileged users to access or modify system files can lead to security breaches, such as unauthorized access to password files or configuration files.
- Solution: Be extremely cautious when modifying permissions on system files. These files should typically have restrictive permissions to ensure only authorized users (e.g., root) can modify them.
chmod 644 /etc/passwd # Ensure proper permissions for sensitive files
Not Verifying Permissions After Changes
- Mistake: Failing to verify the permissions after using
chmod.- Problem: After applying
chmod, it’s important to check that the permissions were set correctly. If you don’t verify, you might inadvertently leave files exposed to unauthorized access or prevent users from accessing the necessary files. - Solution: Use
ls -lorstatto check the file or directory permissions after usingchmodto ensure they were set as expected.
ls -l file_name # Verify permissions after applying chmod - Problem: After applying
Changing Permissions on Sensitive Files Without Backup
- Mistake: Changing permissions on sensitive files without creating a backup first.
- Problem: If you accidentally change the permissions on a critical system file, it could make the system unbootable, or important services might fail. Having a backup of critical files helps recover from mistakes.
- Solution: Always make sure to back up important files before changing their permissions, especially on system files.
cp /etc/passwd /etc/passwd.bak # Backup before making changes
Overusing the chmod Command on Shared Directories
- Mistake: Overusing
chmodon shared directories without considering the needs of all users.- Problem: Shared directories, such as those in multi-user environments, require careful management of permissions to ensure that all users can access the directory while maintaining security.
- Solution: Use group-based permissions and avoid giving too much access to others. Use
chmod g+rworchmod g+rto set the correct group permissions for shared files.
chmod g+rw shared_directory # Allow group members to read and write