
In the world of networking, ensuring the security of network switches and the devices connected to them is a critical task for IT professionals and network engineers. One of the most effective ways to safeguard your network is through switchport security. This concept allows you to control access to switch ports, limit the types of devices that can connect, and prevent unauthorized access to your network.
In this blog post, we’ll explore what switchport security is, why it’s important, and how you can configure switchport security on Cisco switches to prevent malicious activities and enhance network security.
What is Switchport Security?
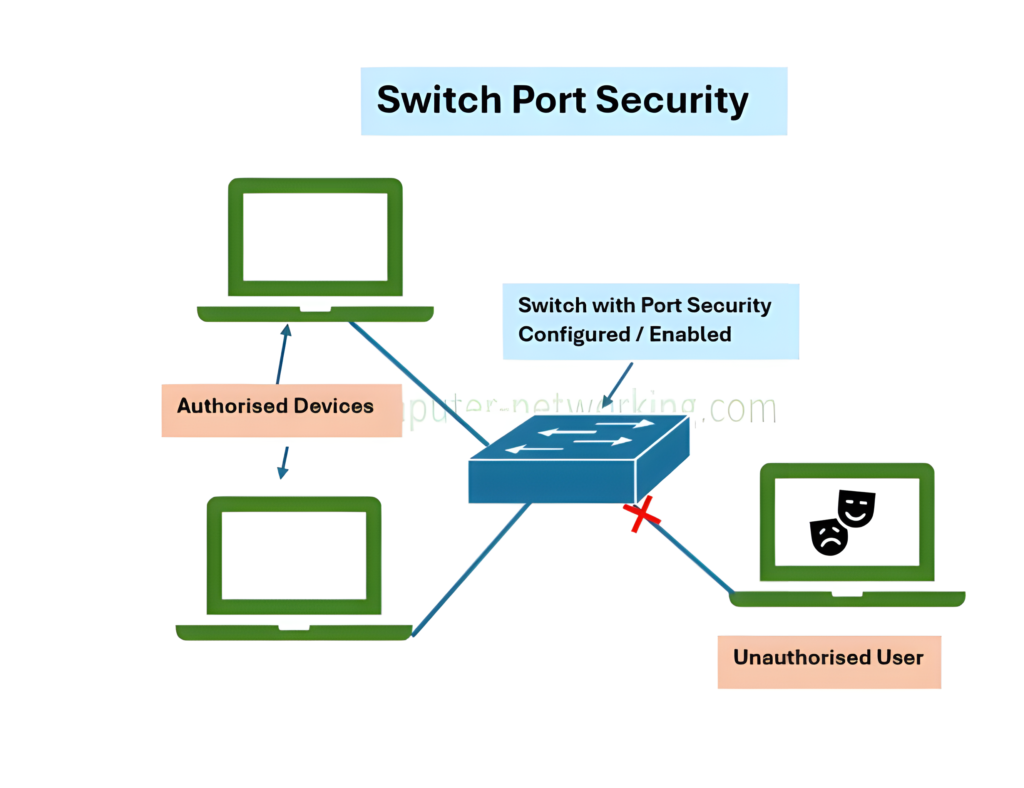
Switchport security is a feature available on many network switches, particularly Cisco devices, that allows network administrators to control access to switch ports based on the MAC addresses of connected devices. Essentially, it’s a security measure that limits and controls which devices can connect to specific switch ports. If a device with an unauthorized MAC address attempts to connect, the switch can take predefined actions such as blocking the connection, shutting down the port, or sending a notification.
Switchport security is an essential tool for preventing common network security threats, such as:
- MAC address spoofing
- Unauthorized access
- Denial of Service (DoS) attacks from rogue devices
- Network sniffing and data interception
Why is Switchport Security Important?
- Prevent Unauthorized Devices: Without switchport security, any device can connect to your network as long as it physically connects to an open switch port. Switchport security ensures that only authorized devices can communicate through the port.
- Minimize Security Breaches: Unauthorized access to your network, whether intentional or accidental, can lead to data breaches, network downtime, or unauthorized changes to the network infrastructure. By implementing switchport security, you reduce the risk of such events.
- Reduce Attack Surface: Attackers often exploit physical access to network ports to launch attacks. By locking down switchports, you make it much harder for attackers to compromise your network.
Key Concepts of Switchport Security
To understand how to effectively use switchport security, it’s important to familiarize yourself with the following core concepts:
1. MAC Address Binding
Switchport security relies heavily on MAC address binding. When a device connects to a switch port, the switch records the device’s MAC address. The switch then allows traffic only from that specific MAC address, thereby preventing any other device from using the same port.
2. Maximum Number of MAC Addresses
Switchport security allows you to define a limit on the number of MAC addresses that can be learned on a port. This is useful for preventing MAC address flooding attacks, where an attacker tries to overwhelm the switch’s MAC address table by flooding it with a large number of fake addresses.
- Example: You might configure a switchport to allow only 2 or 3 devices (MAC addresses) to connect to that port. If more devices attempt to connect, the port will react according to the security settings.
3. Violation Modes
When a security violation occurs (such as when a device with an unauthorized MAC address attempts to access the port), the switch can react in one of the following ways:
- Protect: The switch drops packets from unauthorized devices, but does not disable the port. It silently drops the traffic and does not generate alerts.
- Restrict: Similar to the “Protect” mode, but with the addition of generating an alert. The switch will still drop unauthorized traffic, but administrators are notified about the violation.
- Shutdown: This is the most aggressive violation mode. If an unauthorized MAC address is detected, the port is immediately shut down. This mode is the default and ensures maximum security by preventing any further communication on the port until manually re-enabled.
4. Sticky MAC Address
One of the features of switchport security is sticky MAC address learning. When sticky MAC is enabled, the switch can dynamically learn the MAC address of a device and permanently bind it to the port. This means that even if the device is disconnected and reconnected later, the switch will continue to recognize the MAC address and allow the device to connect.
Sticky MAC addresses help prevent unauthorized devices from using the port, even if the device was previously authorized but is no longer connected.
How to Configure Switchport Security on Cisco Switches
Now that we understand the core concepts, let’s walk through the configuration steps to enable and configure switchport security on a Cisco switch.
Step 1: Access the Switch Configuration
To configure switchport security, you need to be in the global configuration mode of your Cisco switch. Access the switch via the command-line interface (CLI) and enter global configuration mode.
bashCopy codeSwitch# configure terminal
Switch(config)#
Step 2: Enter the Interface Configuration Mode
Choose the interface (port) you want to configure switchport security on. For example, to configure GigabitEthernet 1/0/1, you would enter:
bashCopy codeSwitch(config)# interface gigabitethernet 1/0/1
Switch(config-if)#
Step 3: Enable Switchport Security
Enable switchport security on the interface:
bashCopy codeSwitch(config-if)# switchport port-security
Step 4: Set the Maximum Number of MAC Addresses
Next, define the maximum number of MAC addresses that can be learned on this port. For example, if you want to limit the port to 2 MAC addresses:
bashCopy codeSwitch(config-if)# switchport port-security maximum 2
Step 5: Configure Violation Mode
Set the violation mode to shutdown, restrict, or protect, depending on your preferred action when an unauthorized MAC address is detected. For maximum security, we recommend setting the violation mode to shutdown:
bashCopy codeSwitch(config-if)# switchport port-security violation shutdown
Step 6: Enable Sticky MAC Address Learning
To enable sticky MAC address learning, which dynamically records the MAC addresses of devices that connect to the port, use the following command:
bashCopy codeSwitch(config-if)# switchport port-security mac-address sticky
Step 7: Verify Your Configuration
Once you’ve configured the switchport security settings, it’s important to verify your configuration. Use the following commands to check the status:
bashCopy codeSwitch# show port-security
Switch# show port-security interface gigabitethernet 1/0/1
These commands will show you the number of secure MAC addresses, violation count, and other related information.
Best Practices for Switchport Security
Here are some best practices to ensure your switchport security configuration is both effective and easy to manage:
- Use
shutdownMode for Maximum Security: The shutdown violation mode is the most secure, as it immediately disables the port if an unauthorized device connects. This is particularly useful for preventing malicious access. - Limit the Number of MAC Addresses: Set a reasonable limit for the number of MAC addresses allowed on each port. For most enterprise environments, limiting to 2 or 3 addresses is a good starting point.
- Use Sticky MAC Address Learning for Flexibility: Enable sticky MAC learning on ports that will have devices connected over time, but you still want to prevent unauthorized devices. It provides security while allowing legitimate devices to reconnect.
- Monitor Violation Alerts: Use the restrict violation mode if you want to be notified of violations without shutting down the port. This will provide insight into possible security issues without disrupting normal network operations.
- Regularly Review and Audit Configurations: Switchport security settings should be regularly reviewed and updated to ensure they are in line with the latest security practices and changes in your network.
Application in Different Environments:
Switchport security is beneficial in various environments, such as in office buildings where network ports are accessible in public areas, or in scenarios where a network wants to ensure that only authorized devices have network access.
Conventional network security often focuses more on routers and blocking traffic from the outside. Switches are internal to the organization, and designed to allow ease of connectivity, therefore only limited or no security measures are applied.
The following basic security features can be used to secure your switches and network:
* Physically secure the device
* Use secure passwords
* Enable SSH access
* Enable port security
* Disable HTTP access
* Disable unused ports
* Disable Telnet
Let us look at how to implement and configure some of the above-mentioned switch security features.
How to Configure Switchport Security Example.
How To Configure the Privileged EXEC Password.
Use the enable secret command to set the password. For this activity, set the password to orbit.
SW1#configure terminal
SW1(config)#enable secret orbit
SW1(config)#
Check Cisco Secured Switches on AMAZON
Check Network Security Software on AMAZON
Check Cisco CCNA Network Security Books on AMAZON
How To Configure Virtual Terminal (Telnet) and Console Passwords.
A password should be required to access the console line. Even the basic user EXEC mode can provide significant information to a malicious user. In addition, the VTY lines must have a password before users can access the switch remotely.
Use the following commands to secure the console and telnet:
SW1(config)#line console 0
SW1(config-line)#password cisco
SW1(config-line)#login
SW1(config-line)#line vty 0 15
SW1(config-line)#password cisco
SW1(config-line)#login
SW1(config-line)#exit
SW1(config)#
How To Configure Password Encryption.
At this stage, the privileged EXEC password is already encrypted. To encrypt the line passwords that you just configured, enter the service password-encryption command in global configuration mode.
SW1(config)#service password-encryption
SW1(config)#
How To Configure and test the MOTD banner.
Configure the message-of-the-day (MOTD) using Authorized Access Only as the text. Follow these guidelines:
- The banner text is case-sensitive. Make sure you do not add any spaces before or after the banner text.
- Use a delimiting character before and after the banner text to indicate where the text begins and ends. The delimiting character used in the example below is %, but you can use any character that is not used in the banner text.
After you have configured the MOTD, log out of the switch to verify that the banner displays when you log back in.
SW1(config)#banner motd %Authorized Access Only%
SW1(config)#end
SW1#exit
How To Configure Port Security.
Enter the interface configuration mode for FastEthernet 0/11 and enable port security.
Before any other port security commands can be configured on the interface, port security must be enabled.
SW1(config-if)#interface fa0/11
SW1(config-if)#switchport port-security
* Notice that you do not have to exit back to global configuration mode before entering interface configuration mode for fa0/11.
How To configure the maximum number of MAC addresses.
To configure the port to learn only one MAC address, set the maximum to 1:
SW1(config-if)#switchport port-security maximum 1
How To configure the port to add the MAC address to the running configuration.
The MAC address learned on the port can be added to (“stuck” to) the running configuration for that port.
SW1(config-if)#switchport port-security mac-address sticky
How To Secure Unused Ports.
Disabling unused switch ports is a simple method many network administrators use to help secure their network from unauthorized access. Disabling an unused port stops traffic from flowing through the port(s)
Step 1: Disable interface Fa0/10 on SW1.
Enter the interface configuration mode for FastEthernet 0/17 and shut down the port.
SW1(config)#interface fa0/10
SW1(config-if)#shutdown
Step 2: Disable interfaces Fa0/1 to Fa0/24 on SW1
SW1(config)#interface range fa0/1-24
SW1(config-if)#shutdown
In conclusion, switchport security is a vital component in network security, providing an additional layer of protection by controlling access at the physical port level. It is especially useful in preventing unauthorized or rogue devices from connecting to a network, thereby helping to protect sensitive data and resources.